
Lately, distributed denial of service (DDoS) attacks, and their closely related cousin ransomware attacks, have had quite a renaissance, and I’ve been talking to IT pros and their hiring managers about how to counter them. IT pros often focus on the TTPs involved – the tactics, techniques and procedures and consult threat intelligence feeds and sites such as MITRE’s ATT&CK Navigator to learn more about how to counter DDoS and ransomware attacks. But the C-suite doesn’t really want to geek out at all. They look at DDoS attacks as a business continuity issue.
Mitigating DDoS Attacks: Essential Cybersecurity Skills the Industry Needs Now
The most important thing I’ve learned from responses to DDoS attacks is that you need to work with many different people, applications and equipment. It’s not a single-vendor world anymore. It never was, really!
Besides working closely with people, you’ll need a number of resources, tools and services:
- C-level bosses who want to know how the business is impacted and how to recover
- Your internet service provider (ISP) to help identify and block traffic as quickly as possible
- Third-party scrubbing services, such as CloudFlare and Akamai, that help filter out DDoS traffic
- End-point protection software, such as Zscaler or BitDefender
- Security information and event management (SIEM) tools, such as Splunk or AlienVault
- Security analysts who can isolate traffic and recommend solutions
- A packet capturing tool, like Wireshark, to identify bursts of traffic and, within obvious limits, learn how you can isolate and redirect them into things such as sinkholes and black holes
- Attack visualization software to quickly and effectively identify what is happening when the DDoS attack begins
Cybersecurity Skills the Industry Wants: Visualization and Response
When it comes to visualizing DDoS attacks, there are plenty of public websites that log traffic and identify DDoS attacks. But learning about DDoS attacks has left me feeling a little … flooded.
I’m not kidding.
While trying to learn about the hundreds of protocols and services attackers take advantage of, and myriad ways attackers enlist internet of things (IoT) devices into botnets, I got overwhelmed. But I eventually recovered and took a few small steps to understand how DDoS attacks occur.
First I discovered websites that map DDoS attacks, like Digital Attack Map.
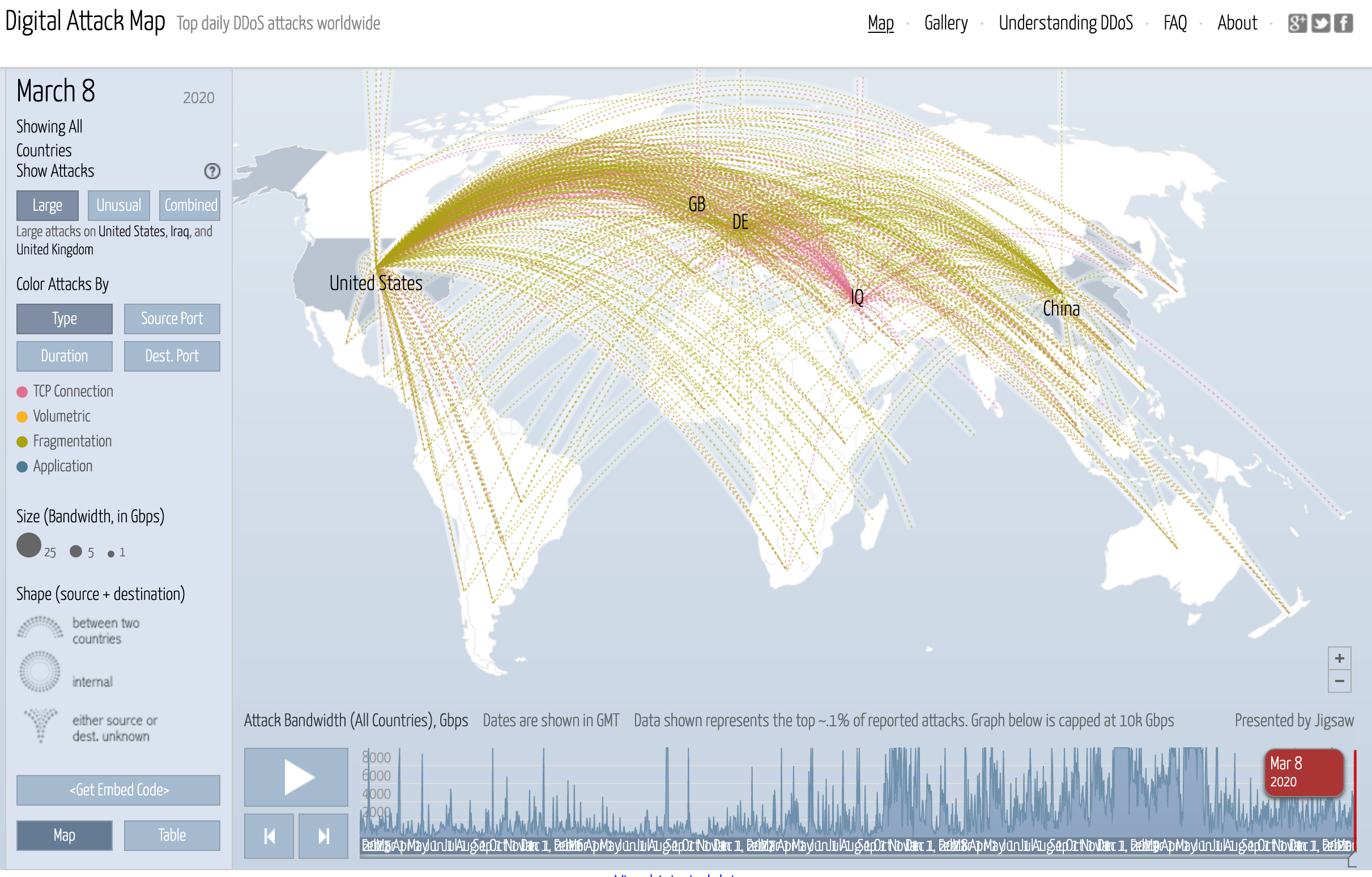
Figure 1: Digital Attack Map tracking DDoS attacks around the world
What’s cool about this site is that you can create simple filters by attack traffic type (e.g., domain name system (DNS)), size or source port. You can even set parameters and then hit the “play” button to watch the attacks go by over time, from as long as five years ago through today.
Sites like NetScout’s DDoS Attack Map, and ThreatCloud map are similar but are too visual for my taste. I could only look at these attacks rather than actually learn more about how they worked.
To get industry-level cybersecurity skills, I needed to conduct and visualize a small DDoS attack myself. So, I set up a DDoS sandbox and dove right in, learning about the essentials of visualizing DDoS attacks of all types.
Playing in the DDoS Digital Sandbox
First, I fired up VirtualBox virtualization software and set up some Linux boxes. I installed an old DDoS application called GoldenEye on one of my Kali Linux systems and used it to wage an attack against a couple other Linux systems on my virtual network. GoldenEye specializes in HTTP-based DDoS attacks. Most IT pros I know use it to conduct stress tests on pre-production web servers.
On another Kali Linux system, I fired up Metasploit, navigated to the auxiliary/dos/tcp/synflood toolset and configured it to create an attack.
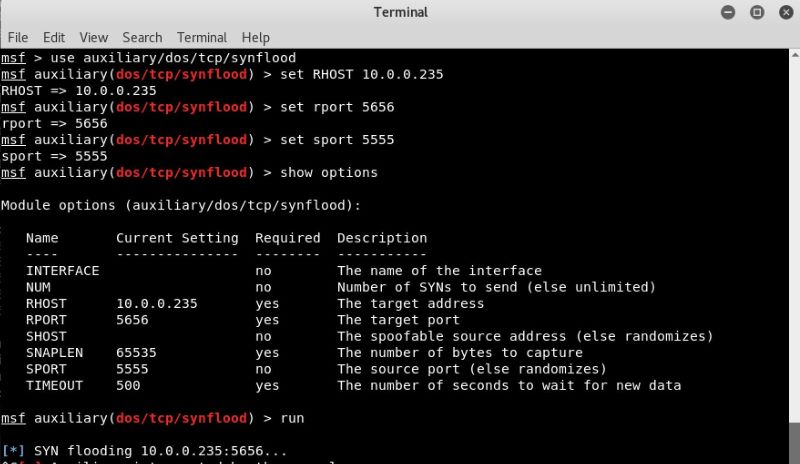
Figure 2: Attacking with Metasploit
I told it to send a SYN flood to port 5656 on the victim system with the IP address of 10.0.0.235. I also told it to use port 5555 as the source port.
Pretty cool, eh? But wait, there’s more!
DDoS Attack Visualization
As a cybersecurity professional, it isn’t enough to just know how to wage an attack. The purpose of this exercise is to learn more about how to visualize and then manage a DDoS attack.
First, I used a monitoring Linux system to sniff the DDoS packets that my Kali Linux system was pumping out into the network. I called on Wireshark, which captured thousands of packets a second.
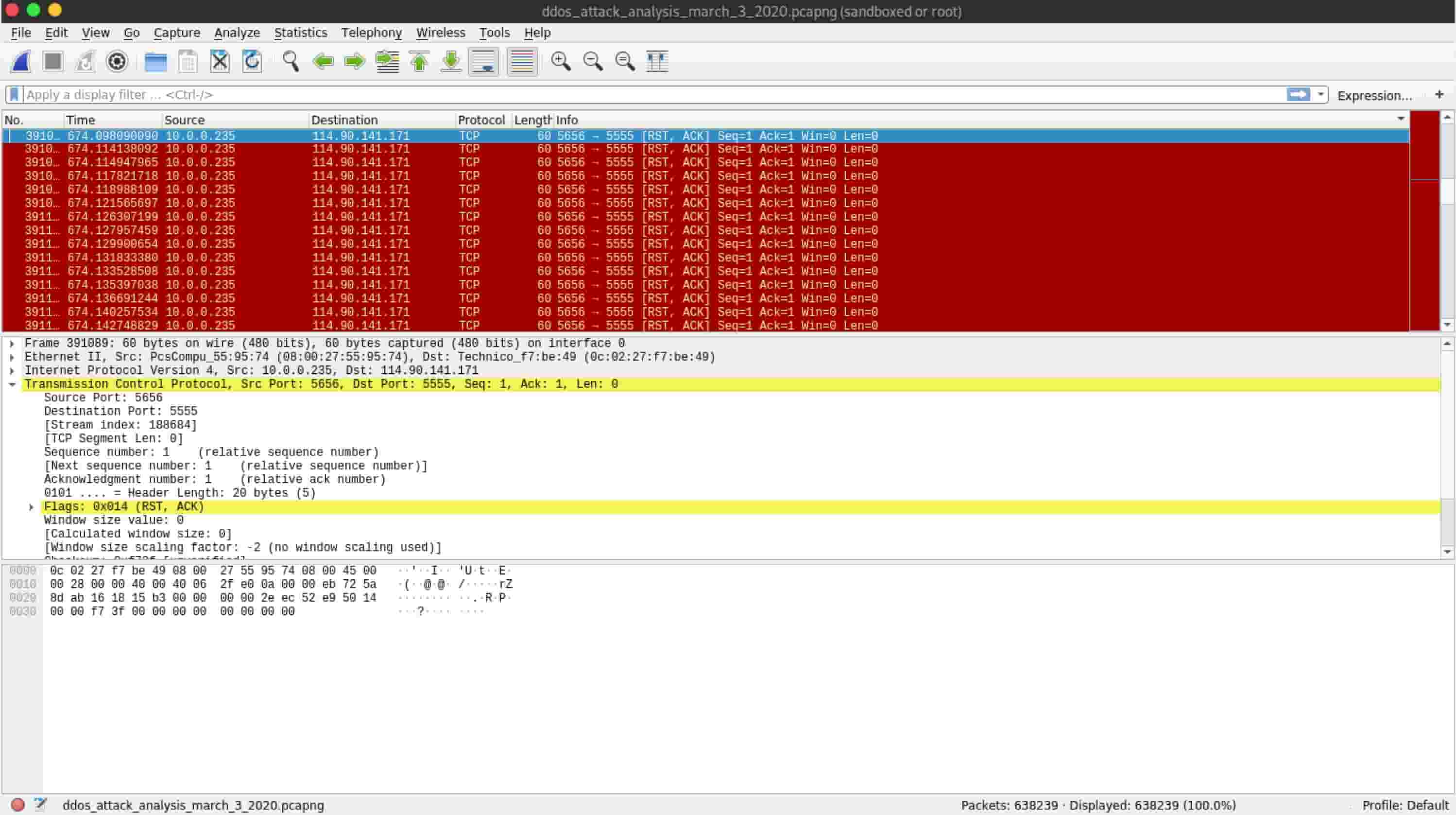
Figure 3: Wireshark showing raw DDoS packets
Notice the IP addresses and ports of the packets that I captured. They’re not very random, are they? Most actual DDoS attacks use spoofed, randomized packets. But I decided to start with the basics and test my ability to forge and then visualize packets.
It wasn’t enough to simply capture those packets – I didn’t get any real context about what was going on, other than watching tens of thousands of packets appear on the screen.
So, in Wireshark, I went to Statistics > IO Graph and brought up two graphics:
1. A graphic to show input/output traffic on my network under normal conditions – how many packets per second my web browser generates when I’m listening to Led Zeppelin’s Physical Graffiti

Figure 4: Wireshark before the attack
2. A second graphic to show what happens when I unleashed GoldenEye and Metasploit on the network

Figure 5: Wireshark during the attack
That’s quite a difference, isn’t it?
Now, this is a pretty basic instance of visualization. But, it sent me down the road of effective DDoS traffic visualization. After a while, I used an application called Etherape to visualize the attack further.
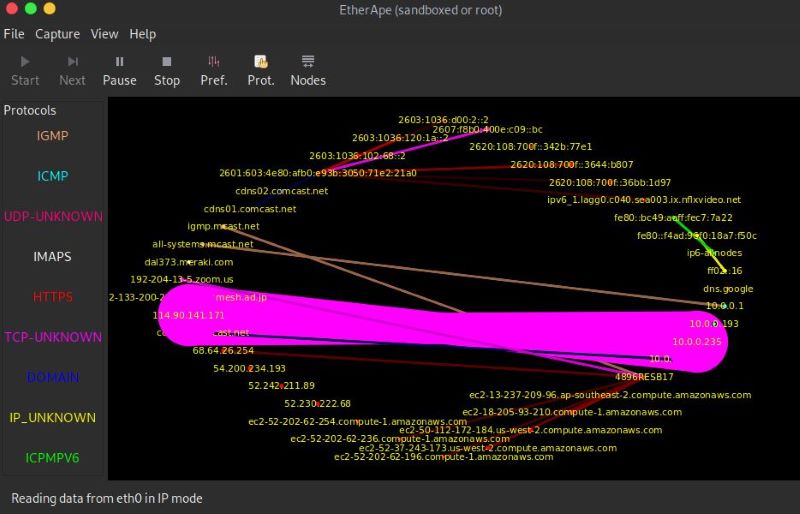
Figure 6: Etherape during the attack
In the above picture, you can see the big, evil, pink stream of traffic. That’s mostly Metasploit doing its evil DDoS thing.
I then graduated from these local, LAN-based tools to SIEM tools, such as Alienvault.
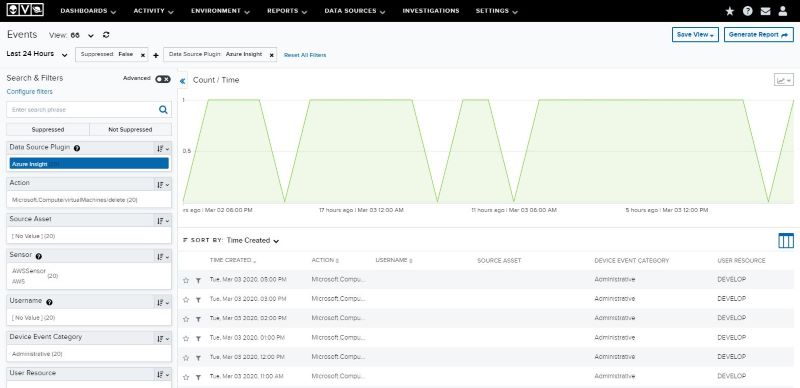
Figure 7: AlienVault showing five DDoS attack instances
When an IT pro, like a junior network technician, for example, tracks these types of DDoS attacks, they may recommend solutions including the following:
- Modifying firewalls
- Segmenting traffic using VLANs
- Using a sinkhole
- Calling up a scrubbing service
- Other, more drastic measures
How to Learn Essential Cybersecurity Skills
As important as visualizing and responding to DDoS attacks is, learning about it can be overwhelming. That’s why we put together a DDOS Handbook. It was designed as a one-stop resource to help you learn about DDoS attacks without becoming too overwhelmed.
In addition to studying, you’ll want to get hands-on practice. That’s what today’s hiring managers are looking for – they want to know that you have some experience actually making phrases such as DDoS TTPs become useful and keep businesses online and working.
Check out our brand new IT pro handbook, What Is a DDoS Attack? A Guide for Protection. You can view it in your browser or download a PDF version for future reference.

