 There’s no denying that cybersecurity is one of the biggest topics in technology today, if not the biggest. Emerging technologies get a lot of headlines because companies are exploring these new trends to find growth opportunities. But at the end of the day, businesses are starting to realize that any new initiative will be short-lived if it is not properly secured.
There’s no denying that cybersecurity is one of the biggest topics in technology today, if not the biggest. Emerging technologies get a lot of headlines because companies are exploring these new trends to find growth opportunities. But at the end of the day, businesses are starting to realize that any new initiative will be short-lived if it is not properly secured.
Making matters more complicated, there is an entirely new approach to cybersecurity. Gone are the days of building a secure perimeter that holds all corporate data and applications. In a cloud and mobile world, businesses have to expand their technology toolbox, build processes for secure operations and educate the workforce on security issues. In this environment, IT pros have to constantly refresh their skills, and CompTIA’s cybersecurity certifications can help keep tech workers ahead of the curve.
However, CompTIA’s latest cybersecurity research study finds that technical skills are not the only ones that security pros need to worry about. As with other parts of digital transformation, cybersecurity is a field where the business side and the IT side need to come together to build the best solution.
Broadly speaking, the business side wants to move very fast, and the IT side wants to be very cautious. Neither end of the spectrum is the ideal place to live, and finding common ground is a challenge for most organizations. Here are three areas where IT pros and business staff have different views on cybersecurity, along with suggestions for how to bridge the gap.
Issue #1: Satisfaction With Current Cybersecurity Practices

IT Pro Viewpoint: 35% Completely Satisfactory
Business Viewpoint: 61% Completely Satisfactory
Next Steps: The common thread throughout the report is that IT pros feel less positive about the cybersecurity situation than their business counterparts. The issue starts at a very high level, with overall satisfaction around the current organizational state of cybersecurity.
This plays out in two key areas where business staff may be less aware than IT pros:
- Current vulnerabilities (assuming the company hasn’t had a major breach yet)
- The relationship between new technology models and new security needs
The first step IT pros should take is giving a clear description of the modern environment — the challenges in cloud/mobile architecture, the breadth of cyberattacks and the tradeoffs involved in balancing innovation and cybersecurity.
Issue #2: Level of Cybersecurity Understanding in the Organization

IT Pro Viewpoint: 38% Very High Level of Understanding
Business Viewpoint: 66% Very High Level of Understanding
Next Steps: There’s a good chance that satisfaction with cybersecurity and understanding of cybersecurity are closely related. Where most business staff feel that the organization has a high level of understanding around the topic, most IT pros feel that there is room for improvement.
After building foundational knowledge around the modern digital environment, IT pros need to describe how today’s security is different:
- There are new technical tools that address issues like data loss or identity management
- There are new processes that mitigate risk or maintain compliance
- And there are new responsibilities for every member of the workforce using technology as part of the job
Most business staff classify cybersecurity as an issue that they want IT to own, but they probably do not understand the degree of complexity involved in organizational security, especially as technology adoption speeds up.
Issue #3: Use of Security Metrics
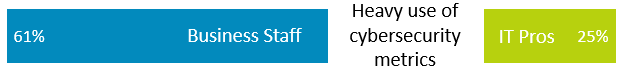
IT Pro Viewpoint: 25% Heavy Use of Metrics
Business Viewpoint: 65% Heavy Use of Metrics
Next Steps: Feeling good about cybersecurity or understanding the issues involved are hard to measure, but tracking progress should not be. Using metrics for cybersecurity is a relatively new concept. In the past, most companies would claim success if there were no security breaches (that they knew about). But in today’s environment, a security breach can go months without being detected, causing damage the whole time.
IT pros can take the lead on building consensus around the metrics that matter for the organization and reporting on progress to help justify any investments being made.
Some commonly used metrics include the following:
- Number of successful security audits
- Percentage of employees who have been through security training
- List of systems that have had a formal risk assessment
Most companies are trying to break down silos and build a collaborative environment for discussing technology. In this environment, the business units can describe goals and time frames, and IT can describe tradeoffs and possibilities. This strategic approach is in its early stages, and coming to agreement on risk tolerance and cybersecurity actions will be a major ingredient in moving the discussion forward.
To learn more about the way that the cybersecurity function is evolving, download Cybersecurity for Digital Operations.

