 You don’t have to be an IT pro to understand the following maxim: Automate, or get automated. We’ve all seen the effects of automation over the years. IT pros are long past the days of writing only batch and shell scripts to automate tasks. With the advent of sophisticated data centers and cloud implementations, workers in nearly every job role need to know how to automate sophisticated tasks.
You don’t have to be an IT pro to understand the following maxim: Automate, or get automated. We’ve all seen the effects of automation over the years. IT pros are long past the days of writing only batch and shell scripts to automate tasks. With the advent of sophisticated data centers and cloud implementations, workers in nearly every job role need to know how to automate sophisticated tasks.
It doesn’t matter if you are a technical support specialist, cloud DevOps engineer or security analyst. You need skills in automated configuration management. We have so many devices and systems. Even the best command line hot shot can’t manage every instance. You need to automate.
Automated Configuration Management Tools
So many configuration management platforms exist to help automate tasks, including those listed in the table below. The goal behind these tools is to conduct sophisticated tasks on multiple remote systems with as little human involvement as possible.
Common IT Automation Tools
| Tool | Description and Characteristics |
| Uses the YAML language to create sophisticated scripts, which are called playbooks, and relies upon Secure Shell (SSH), rather than a separately installed agent, to connect to remote systems | |
| Uses the term “recipe” to describe resources you wish to manage and the term “cookbook” to describe how to automate the process of managing resources; uses the Ruby language to create scripts | |
| Uses the term “manifest” to describe each resource (a server or an internet of things (IoT) device) and then uses the term “module” to describe the tasks you wish to automatically manage; scripts are created using the PuppetDSL language | |
| Uses either HashiCorp Configuration Language (HCL) or JSON to create modules, which describe the tasks you wish to automate |
The tools listed above are either open source or have open-source versions. There are many more configuration management tools available, but I’ve been hearing about these lately. Let’s take a closer look at Ansible.
Setting the Foundations For Ansible
Because Ansible doesn’t use its own installed agents to help you automate tasks, it relies upon the following underlying services to run properly:
- Secure Shell (SSH): The de facto standard for managing remote systems. You will want to configure SSH for public key authentication before using Ansible.
- Domain Name System (DNS): While not absolutely necessary, it’s always a good idea to have a solid, working DNS implementation in your network.
To get started with Ansible, you’ll need to meet the following conditions:
- Ansible installed on all systems you wish to manage
- Sufficient permissions to issue commands on remote systems
- A valid Ansible playbook
Running a Playbook with Ansible
If you want to use Ansible to automate the configuration of remote servers, you’ll need to create a playbook. Figure 1 shows a relatively simple example named ubuntu_clean.yaml.
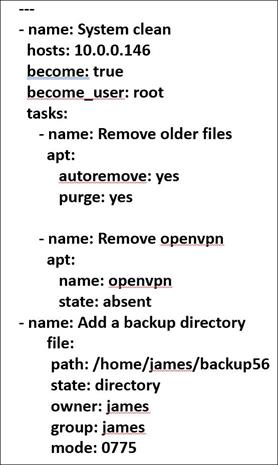
Figure 1: Ansible playbook example
In this example, I’m cleaning up a single remote Ubuntu Linux system by first removing older files from its apt-get cache. The apt-get utility is used in Linux systems to install, remove and manage applications and services, much like the Windows Add/Remove utility from Control Panel. Using the autoremove command in apt-get is sometimes necessary to free up disk space.
I then tell Ansible to remove the openvpn utility from that system in this playbook. There’s nothing wrong with openvpn; I use it all of the time to create Virtual Private Network (VPN) connections. But, for the Linux server I’m configuring, I don’t need openvpn installed.
I then have told Ansible to create a remote directory that I will use to store some backup files. Notice that I can even set permissions exactly the way I want them on that directory; granular control is possible using Ansible, or any similar tool.
Normally, I would have to issue several different commands to accomplish these tasks. But, now that I’ve configured this Ansible playbook, I can get each of these tasks done with just one command:
$ ansible-playbook ubuntu_linux_system_maintenance.yaml --extra-vars "ansible_sudo_pass=ubuntu123"
Figure 2 below shows the results of the successful playbook.
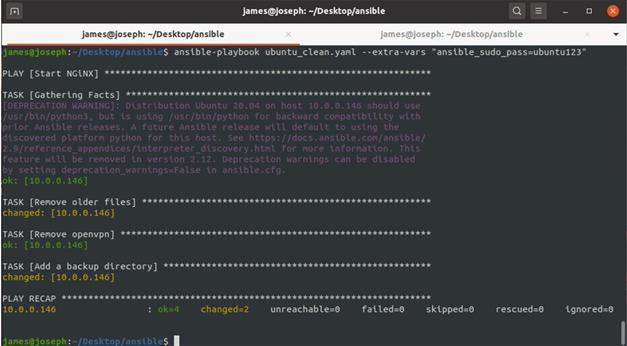
Figure 2: Ansible completing its tasks
You’ve now seen a simple example of how you can use Ansible to configure a remote system. Imagine if I had 20 more Ubuntu Linux systems that needed the same attention. Instead of running multiple commands on each system manually, all I need to do is specify the IP addresses or DNS names of those additional systems in my playbook. With one command, I can manage all of those remote systems in a matter of seconds.
Pretty cool, huh? And that’s just a simple example of the sophisticated tasks you can automate and eventually orchestrate using a tool like Anisble.
I talk regularly with IT pros who use Ansible to remotely administer hundreds of remote systems, both in data centers and in the cloud. They say they couldn’t do their jobs without it.
Getting Hands-on Practice
You don’t have to use Ansible, of course. Many other tools exist. If you’re learning, I highly recommend that you get a good underlying IT infrastructure going and then delve into one or more of the automation tools I’ve listed above. As you move from simple “hello world” types of scripts into more sophisticated playbooks, recipes and cookbooks, you’ll find yourself in high demand, both in the cloud and the data center.
CompTIA Server+ and CompTIA Cloud+ cover the skills needed for data center and cloud automation. Check out our article on how to choose between Server+ or Cloud+ to learn more. Or, if you know which certification is right for you, download the exam objective for free to start studying.

