
The Open Systems Interconnection (OSI) model is a series of layers through which computer systems use to communicate. There are seven layers, and the networking layer would be layer 3. The network layer is responsible for packet forwarding, including routing through intermediate routers. However, when it comes to understanding network data delivery, we need to get through layer 2 before we can move on to layer 3.
The data link layer, or layer 2, is the protocol layer that transfers data between nodes on a network segment across the physical layer, or what is commonly known as a host’s physical address. Layer 2 is divided into two parts, consisting of the MAC and data link sublayers, detailing addressing and the layout of data frames, and Layer 3 includes a host’s logical address. Let’s take a closer look at how these layers work together to ensure a delicious flow of data.
What Are the Seven Layers of the OSI Model?
Before we dig deep into layers 2 and 3, let’s start with a little bit of background on the Open Systems Interconnection (OSI) model. The OSI model was developed by the International Organization for Standardization (ISO). It describes the layers that computer systems use to communicate over a network and was the first standard model for network communications adopted by all major computer and telecommunication companies in the early 1980s.
The OSI model has seven layers:
- Physical
- Data Link
- Network
- Transport
- Session
- Presentation
- Application
What Is Layer 2 in the OSI Model?
As mentioned above, layer 2 is split into two parts: The media access control (MAC) sub layer and the data link sub layer. These sub layers each do their part to make up the computer’s physical address.
Media Address Control (MAC) Sub Layer
To gain an appreciation of the characteristics of addressing, it is helpful to bring forward an example that may be familiar and easy to understand.
Let’s think about this in terms of a mobile home community. Each of the mobile homes have a serial number permanently attached to the home’s frame. Computers have a similar address, called its media access control (MAC) address. That address is “burnt” on to the computers network interface card and is unique in nature. An example of the MAC address is shown in figure 1 below.

Figure 1: Media Access Control (MAC) address
MAC (or physical) addressing provides an effective method of moving data across a small community of computing devices where routing traffic between multiple communities is not required. Traffic distribution for these small networks is handled by layer 2 switches that learn the MAC addresses of the computers connected to ports on the switch. The switches then send packets from the sending computer directly to the receiving device. This method of directing traffic helps reduce potential network congestion.
A MAC address consists of a series of 12 hexadecimal numbers. The first six numbers are useful in identifying the manufacturer of the network interface card. The last six numbers are assigned by the card manufacturer, providing a unique addressing scheme. This avoids the possibility of having two computers on the same network with the same physical address.
Data Link Sub Layer
Another layer 2 function is to establish protocols that relate to the structure of data frames that are placed on the network for data transmission. Uniformity is an important characteristic and includes placing both addresses for the data sender as well as the data recipient. Figure 2 below provides an example of an Ethernet II frame.
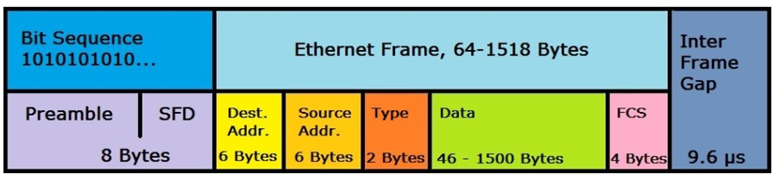
Figure 2: Ethernet II frame
Each frame includes the MAC address of the source of the frame and the MAC address of the intended recipient. When a device sends a packet to the broadcast MAC address (FF:FF:FF:FF:FF:FF), it is delivered to all stations on the local network.
In the early days of networks, MAC addressing worked well, with only a few computing devices on a single flat network. Because of this, it was unnecessary to extend the network past its limited physical boundaries. Through a process associated with linking a computing device name to its MAC address, either by way of a table or through broadcast protocols like Microsoft’s NetBEUI, devices were able to effectively communicate.
However, as networks grew, network traffic grew and traffic congestion became problematic. As a consequence, a second layer of addressing designed to facilitate connecting two or more networks together became necessary to deal with both traffic congestion and latency issues. Thus, the data link sub layer was born.
Understanding OSI Layer 3
Commonly referred to as the networking layer of the OSI model, layer 3 provides the structure relating to how data can be efficiently transferred from one network to another. Let’s go back to the mobile home community example.
When a unit is placed in a mobile home community, it is typically located on a lot (often referred to as a space). The lot address can be used for postal service purposes. As you know, if you want to mail a package from one mobile home to another, serial numbers won’t work. But if you address the package properly, using the format the postal service requires, we have some assurance of delivery.
When it comes to computer networking, our postal service consists of computing devices known as routers. Functioning at layer 3 requires the creation of an outside envelope over the layer 2 frame, that includes the layer 3 address of the sender of the packet, along with the layer 3 address of the recipient.
Layer 3 addresses are divided in a fashion that identifies a specific network address and a specific host or group of hosts. When it is determined that the recipient’s network address is different from the sender’s network address, packets are directed to the network’s router for delivery handling.
In today’s modern networking, we use the TCP/IP suite of protocols for communication that crosses networks. The postal service provides a vehicle for understanding how logical addressing using IP protocol works.
Using the logic address above, the postal service would be able to deliver a package based upon the following:
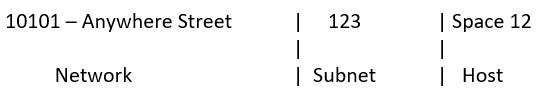
Using the IP (version 4) addressing scheme for the IP address 172.16.1.12/24, the address breaks out as:
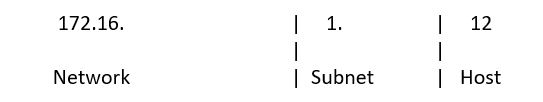
The processes and procedures associated with logical networking as it relates to subnetting and supernetting are beyond the scope of this article.
What is important is that you understand that a portion of an IP address is allocated for both network and host identification. Devices that are located on the same network will be able to communicate effectively at layer 2. Devices that are on different networks will communicate by directing their output data to routers that will be charged with the responsibility of delivery.
Get Started With CompTIA Network+
If computer networking piques your interest, CompTIA Network+ can help you develop your IT career. CompTIA Network+ certification holders are often hired as network field technicians, engineers, analysts and support specialists – just to name a few.

Technology employers hire IT pros with CompTIA Network+ because the credential ensures you have the knowledge and skills to do the following:
- Design and implement functional networks
- Configure, manage and maintain essential network devices
- Use devices such as switches and routers to segment network traffic and create resilient networks
- Identify benefits and drawbacks of existing network configurations
- Implement network security, standards and protocols
- Troubleshoot network problems
- Support the creation of virtualized networks
There are a variety of ways to start studying for CompTIA Network+, including self-study eLearning with CertMaster Learn or CompTIA Labs, using the Official CompTIA Network+ Study Guide or taking CompTIA live online instructor-led training. (P.S. I currently teach with CompTIA.)
Want to start a career in computer networking? CompTIA Network+ can help you get there. Download the exam objectives for free to get started.
Steve Linthicum taught cybersecurity courses for decades as a professor at the college and university levels. He holds an array of IT and cybersecurity industry certifications, including CompTIA Certified Technical Trainer (CTT+)

