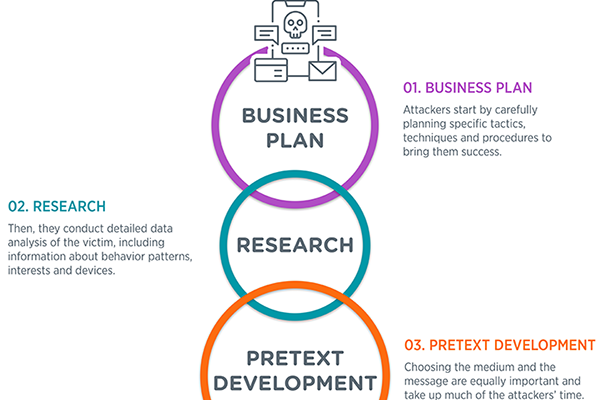
The Process of Social Engineering
Understand the process so you can protect your organization.7/12/2022 | Infographic

7/12/2022 | Infographic

7/1/2022 | Whitepaper

6/30/2022 | Use Case

6/9/2022 | Research

6/8/2022 | Article

6/3/2022 | Guide

5/23/2022 | Article

5/12/2022 | Use Case